Author: Ruchir Shastri
Key Differences Between VPS and Dedicated Servers
We all want the best hosting servers for our projects, and there are two of the most reliable hosting solutions are VPS and Dedicated server. However there are number of reasons why one should opt for dedicated server instead of a VPS, six of which are listed ...
Control Panel for Linux Servers – cPanel / WHM
Control Panel is one of the various important aspect that need strict attention when choosing your web hosting. Control Panel is a wonderful tool to manage both your website and virtual environment. There are wide range of control panels available in web hosting market that can somehow complicate ...
Advantages of SSD Hosting
Introduction
SSD stands for Solid State Drives. With SSD based server, access time of websites, databases, E-Commerce applications speeds up significantly. When a visitor is on look out for information on specific topic and in case it is not available at one address, they will shift and search at some ...
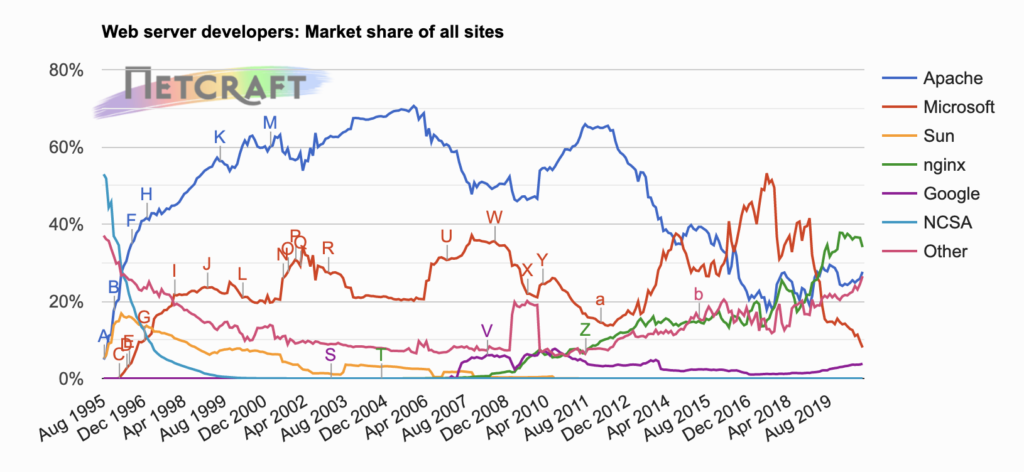
Introduction to Web Server Software – 2020 Update
A web server has many purposes – can be used to host a website, runs enterprise applications, can act as a data storage or even as a game server. In other words, web servers are computers that help with online content accessibility through the Web.
A web server can be referred to as both hardware and software.
Hardware (computer) – it is used to host web applications ...
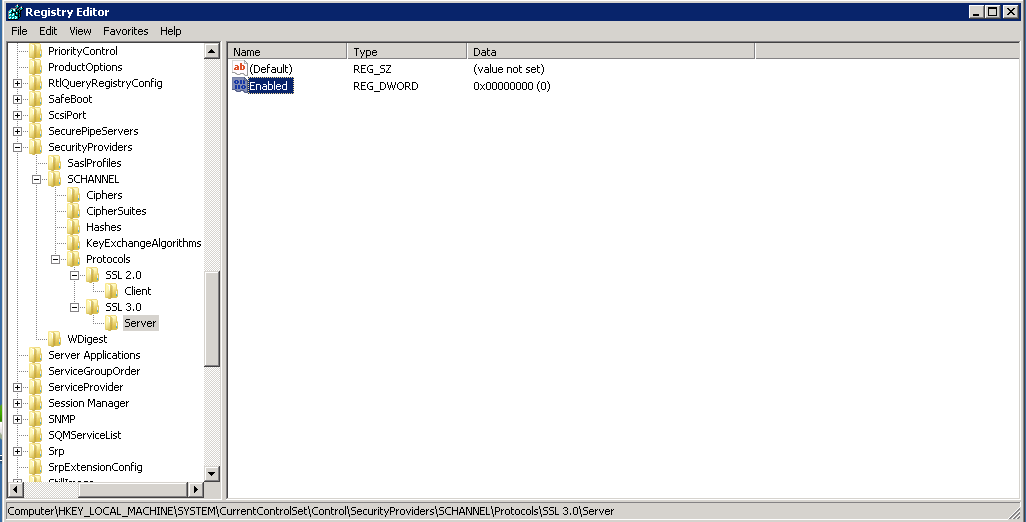
How to protect Windows IIS server from SSLv3 POODLE bug
As a quick fix to protect your Windows server machines from the latest SSLv3 POODLE bug, please follow below steps on your Windows Server machine - these steps essentially disable the vulnerable SSLv3 protocol:
1) Open registry editor and navigate to
HKey_Local_Machine\System\CurrentControlSet\Control\SecurityProviders\ SCHANNEL\Protocols
2) You will likely see an entry with SSL ...
Web Hosting Factors That Affect SEO Rankings
SEO is a continuous process to be incorporated in your promotional activities to succeed online. Creating and making website online is like ‘Wow, I got a website and now I will start getting orders’. Sure, you are on right path for online success but there is an ...
Security Advisory – Critical Bash Shell Vulnerability – Fix Available
A vulnerability has recently been disclosed in Bash (the GNU Bourne Again shell) which affects all systems running Linux. This vulnerability allows programs that allow users to provide values for variables to execute arbitrary commands with the privileges of the service. This issue does not permit direct ...
HTTPS / SSL Encryption – Do it for web security or Google Ranking Boost?
Google is working to make the internet safe and to take an initiative, they have adopted HTTPS encryption for their own main domain and sub-domains. It means, a secured connection is setup every time when accessing Google Search, Gmail and Google drive sub-domains.
After months of experiment in ...
How To Change SSH Port Of Linux Server
There are lot of brute force attacks over default service ports and hence it is highly recommended to change the default port as a first steps security measure. The default SSH port of Linux distros is 22. You can change this to something else by following below steps:
1) Login ...
Managed Hosting: Server Management and Monitoring Services
Over a period of time, many industries have spent huge amount of resources and money for managing their server onsite and offsite as there were near to no options available in the past for this. Thanks to evolving hosting industry, we now have quite a few options ...